Trust-based electronic signature
Enable document signing with pre-verified identities and device trust assessment
Enables document signing for users who already have verified AML identity data, while intelligently adapting the flow based on device trust signals to balance security and user experience.
In this recommended flow, the customer’s system uses existing AML-compliant identity data from a previous verification to issue a signature without requiring users to repeat full identity proofing. Before the signature is created, the platform performs a device trust assessment, evaluating behavioral and technical signals to determine whether the device and network environment appear safe.
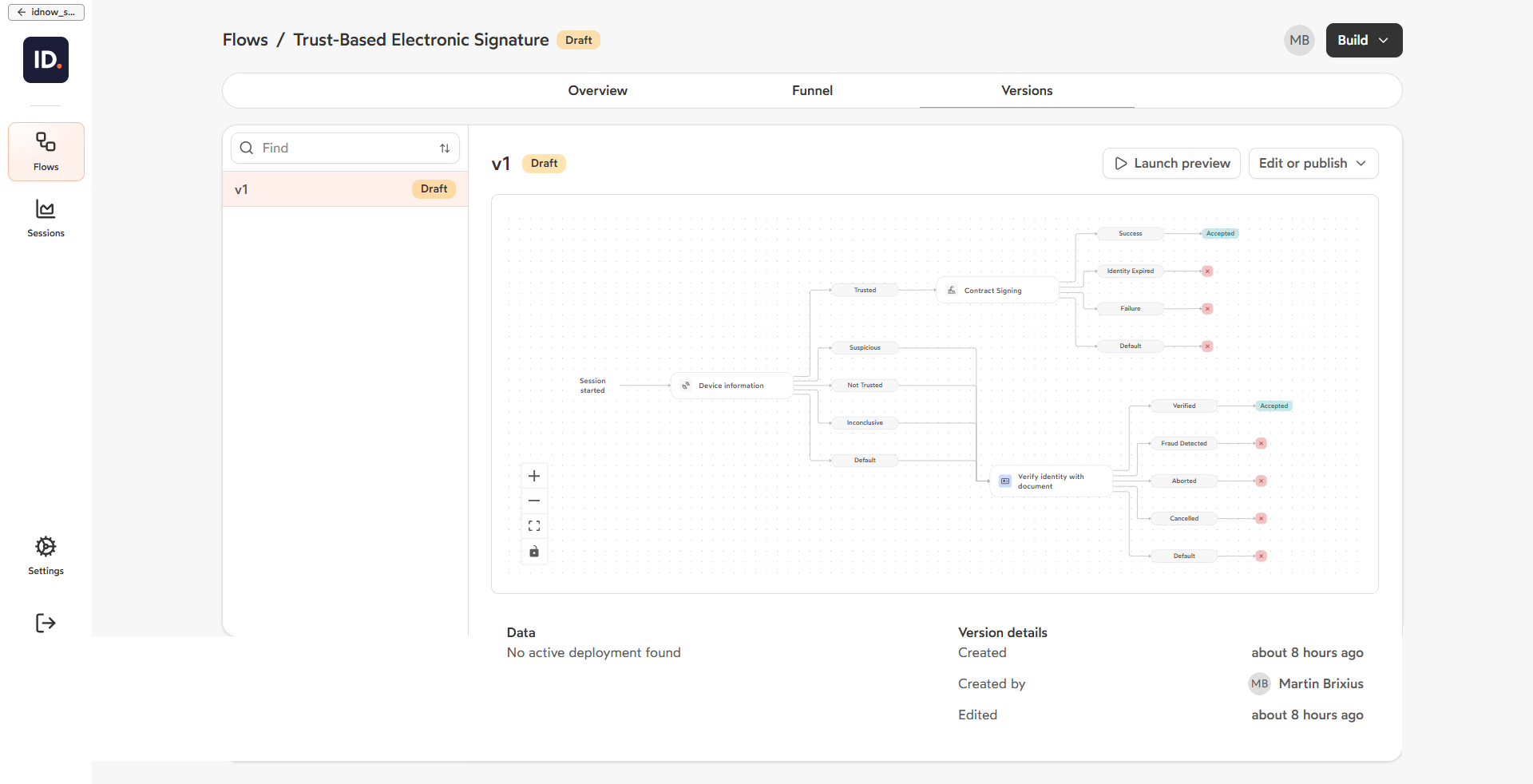
If the environment is trusted, the process continues seamlessly using the stored identity data. If the environment is suspicious or untrusted, the flow introduces a light dynamic verification step, prompting the user to provide a fresh set of identity evidence. This adaptive approach applies “healthy friction” only when risk is detected, ensuring compliance and fraud prevention while maintaining a smooth experience for low-risk users.
This trust-based signature flow helps organizations optimize security, compliance, and user experience, protecting against identity misuse and device-based fraud while keeping high completion rates.
Key benefits
- Adaptive trust decisioning – Dynamically routes sessions based on device and network risk signals.
- Frictionless experience for trusted users – Enables immediate signing using existing AML identity data.
- Healthy friction for suspicious sessions – Requests renewed verification only when anomalies are detected.
- Optimized risk and UX balance – Strengthens fraud prevention without compromising conversion.
- Compliance-ready – Maintains alignment with AML and eIDAS requirements for secure electronic signatures.
Flow Logic
Step overview
| Step | Purpose |
|---|---|
1. Start | Entry point; collects input DataBlocks |
2. Device intelligence | Analyzes device trustworthiness |
3a. Instant signature issuance | Enables document signing (trusted path) |
3b. Document-based IDV (Capture) | Verifies identity via. Document-based IDV (untrusted path) |
4. End | Final decision: accepted or rejected |
Verdict Routing
This flow uses a risk-based routing mechanism where verdicts at each step determine the next action. Trusted devices proceed directly to signing, while untrusted or suspicious devices require additional identity verification.
| Step | Verdict | Meaning | Action |
|---|---|---|---|
| Device intelligence | trusted | Device recognized, normal behavior | Proceed to Instant signature issuance |
| Device intelligence | suspicious, not_trusted, inconclusive, else | Unknown device or anomalies detected | Route to Document-based IDV (Capture) |
| Instant signature issuance | success | Signing completed successfully | Session outcome accepted |
| Instant signature issuance | identity_expired | Pre-verified identity exceeded validity period | Session outcome rejected |
| Document-based IDV (Capture) | verified | Identity confirmed via Document-based IDV | Session outcome accepted |
| Document-based IDV (Capture) | fraud_detected, aborted, cancelled, else | Fraud, user abandonment, or errors | Session outcome rejected |
Configuration
Device signals
| Parameter | Type | Description |
|---|---|---|
suspiciousUserThreshold | integer (≥0) | Threshold for "suspicious" classification based on suspectScore |
notTrustedUserThreshold | integer (≥0) | Threshold for "not_trusted" classification based on suspectScore |
confidenceScoreThreshold | float (0-100) | Minimum fingerprint confidence; below this value result is "inconclusive" |
Example:
{
"suspiciousUserThreshold": 50,
"notTrustedUserThreshold": 75,
"confidenceScoreThreshold": 60
}
Instant signature issuance
| Parameter | Type | Description |
|---|---|---|
signingConfiguration.signatureLevel | enum | QES or AES (required) |
Signature levels:
| Level | Legal effect | Required input data blocks |
|---|---|---|
| QES | Equivalent to handwritten signature (eIDAS). Requires strict identity verification. | ExtendedIdentity, DocumentData, DocumentsToSign |
| AES | Uniquely linked to signer. No regulated identity-proofing required. | ExtendedIdentity, DocumentsToSign |
Example:
{
"signingConfiguration": {
"signatureLevel": "QES"
}
}
Input data blocks
Provide these data blocks when creating a session:
| Data block Type | Description | Required For |
|---|---|---|
BasicIdentity | Pre-verified identity data | All flows |
DocumentData | Identity document information | QES signature level |
DocumentsToSign | Documents requiring signature | All flows |
Note: DeviceSignals are auto-collected by Trust Platform.
Output data blocks
Trusted device path
When device signals indicate high trust and signature succeeds:
| DataBlock Type | Created By | Description |
|---|---|---|
DeviceSignals | device_signals | Device trust assessment results |
SignedDocumentsPackage | Instant signature issuance | Signed documents and metadata |
Untrusted Device Path
When device signals trigger identity re-verification:
| Data block type | Created By Step | Description |
|---|---|---|
DeviceSignals | Device Signals | Device trust assessment results |
DocumentImages | Document-based IDV (Capture) | Uploaded document images |
DocumentData | Document-based IDV (Capture) | Extracted document data |
ExtendedIdentity | Document-based IDV (Capture) | Verified identity data |
BiometricSamples | Document-based IDV (Capture) | Liveness/selfie capture |
DocumentVerification | Document verification step | Verification results |
SignedDocumentsPackage | Instant signature issuance | Signed documents and metadata |
API integration example
Scenario: Trusted device completes signature successfully
1. Create session
Request: POST /v1/flows/{flowId}/{environment}/sessions
{
"input": [
{
"type": "ExtendedIdentity",
"familyName": "Schmidt",
"givenName": "Max",
"birthDate": "1985-08-22"
},
{
"type": "DocumentData",
"documentType": "ID",
"documentNumber": "T22000126",
"issuanceDate": "2020-05-10",
"expiryDate": "2030-05-10",
"issuingCountry": "DE"
},
{
"type": "DocumentsToSign",
"documents": [
{
"templateId": "tmpl_loan_agreement_v2",
"sourceUrl": "https://storage.idnow.io/docs/loan_789.pdf"
}
]
}
]
}
2. Check session status
Request: GET /v1/{environment}/sessions/sess_abc123
Response:
{
"flowId": "40cbb7b3-7468-4b5d-8bb5-ff8e82510c70",
"flowVersion": 1,
"environment": "live",
"subjectId": "customer_ref_12345",
"sessionId": "sess_abc123",
"sessionStatus": "completed",
"createdAt": "2025-12-18T10:30:00Z",
"startedAt": "2025-12-18T10:30:15Z",
"updatedAt": "2025-12-18T10:32:45Z",
"completedAt": "2025-12-18T10:32:45Z",
"expiresAt": "2025-12-18T22:30:00Z",
"outcome": "accepted",
"lastStep": {
"stepName": "END",
"stepType": "STEP",
"verdict": "accepted"
}
}
3. Retrieve Data blocks
Request: GET /v1/{environment}/sessions/sess_abc123/datablocks
Response:
{
"datablocks": [
{
"type": "DeviceSignals",
"createdByStep": "device_signals",
"userReference": "customer_ref_12345",
"provider": "Fingerprint",
"timestamp": "2025-12-18T10:30:18Z",
"services": ["device", "ip", "browser"],
"inputSources": {
"extendedIdentity": "session_started"
},
"result": "trusted",
"score": 85,
"reasons": [
{
"code": "DEVICE_RECOGNIZED",
"details": "Device previously used for successful transactions"
}
],
"signals": {
"deviceId": "dev_xyz789abc",
"ipAddress": "192.168.1.100",
"browser": "Chrome/120.0",
"os": "Windows 11",
"vpnDetected": false
}
},
{
"type": "SignedDocumentsPackage",
"createdByStep": "Instant_signature_issuance",
"signatureProcessId": "tx_987654321",
"signedDocuments": {
"mode": "both",
"archiveUrl": "https://storage.idnow.io/signed/archive_abc123.zip",
"documents": [
{
"templateId": "tmpl_loan_agreement_v2",
"signedUrl": "https://storage.idnow.io/signed/loan_789_signed.pdf"
}
]
},
"createdAt": "2025-12-18T10:32:45Z"
}
]
}